القرصنة الأخلاقية - أدوات لمراحل القرصنة الخمس
هذا المنشور جزء من سلسلة تسمى "القرصنة الأخلاقية".
أثناء دراستي للحصول على هذه الشهادة ، سأقوم بتحديث هذه المشاركة بمجموعة متنوعة من الأدوات والمواقع الإلكترونية المفيدة. استخدم هذه الأدوات فقط في بيئتك الخاصة للأغراض التعليمية فقط.
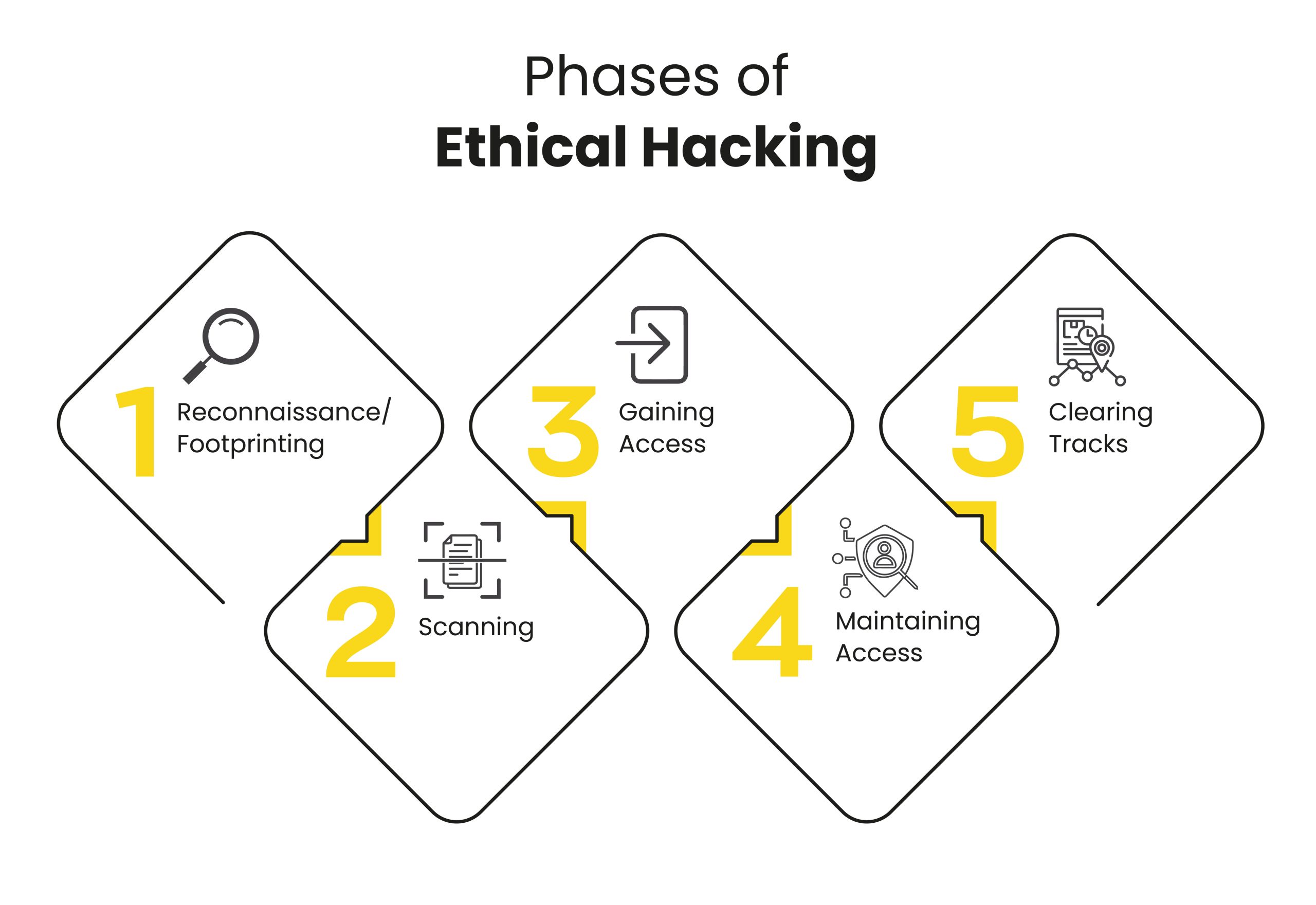
هناك 5 مراحل للقرصنة ، تلك المراحل هي (بالترتيب) :
===> قد تظهر بعض الأدوات المدرجة أدناه في أكثر من مرحلة واحدة.
1 - استطلاع (Reconnaissance)
- Archive.org
- See cached versions of websites.
- Google Maps
- See psychical locations.
- Netcraft.com
- See what OS websites servers are running, the DNS admin, hosting history, hosting company, site technology and a lot more.
- Google Alerts
- Get alerts to get any new information from websites.
- Google Hacking Database
- Predefined Google advanced operators.
- Google Advanced Operators
- Advanced Google searching.
- Firebug
- View source code and a lot more.
- Web Data Extractor
- Extract information (metadata) from a website.
- HTTrack
- Takes a full copy of a website and make it offline.
- Metagoofil
- Metagoofil is a tool for extracting metadata of public documents (pdf,doc,xls,ppt,etc) available in the target websites.This information could be useful because you can get valid usernames, people names, for using later in bruteforce password attacks (vpn, ftp, webapps), the tool will also extracts interesting “paths” of the documents, where we can get shared resources names, server names, etc.
- eMailTrackerPro
- Analyze e-mail headers and generate reports with WHOIS information, spam filter etc.
- Wireshark
- Wireshark is a free and open source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 due to trademark issues.
- MXToolbox
- Analyze e-mail headers, inspect domains, block list, DNS Lookup and a lot more.
- WHOIS (Kali Linux)
- Shows the registrant, admin, name server information etc.
- DomainTools
- Whois lookup information.
- SmartWhois
- SmartWhois is a useful network information utility that allows you to look up all the available information about an IP address, hostname or domain, including country, state or province, city, name of the network provider, administrator and technical support
- nslookup
- nslookup is a network administration command-line tool available for many computer operating systems for querying the Domain Name System (DNS) to obtain domain name or IP address mapping or for any other specific DNS record.
- Network-Tools.com
- DNS records tool that retrieves the domain name records for a specified domain.
2 -المسح (Scanning)
- Nmap
- Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing.
- Scapy
- Scapy is a powerful interactive packet manipulation program. It is able to forge or decode packets of a wide number of protocols, send them on the wire, capture them, match requests and replies, and much more.
- hping3
- hping is a command-line oriented TCP/IP packet assembler/analyzer. The interface is inspired to the ping(8) unix command, but hping isn’t only able to send ICMP echo requests. It supports TCP, UDP, ICMP and RAW-IP protocols, has a traceroute mode, the ability to send files between a covered channel, and many other features.
- telnet
- Telnet is a protocol used on the Internet or local area networks to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection. User data is interspersed in-band with Telnet control information in an 8-bit byte oriented data connection over the Transmission Control Protocol (TCP).
- nc
- Netcat is a simple Unix utility which reads and writes data across network connections, using TCP or UDP protocol. It is designed to be a reliable “back-end” tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. Netcat, or “nc” as the actual program is named, should have been supplied long ago as another one of those cryptic but standard Unix tools.
- ID Serve
- ID Serve is a freeware by Steve Gibson is essentially a security investigation tool. Its main function is to examine the workings of the Web server. This program also gives information in the operating platform of the server. The probe can also reveal useful information on other information such as cookie values and reverse DNS information.
- Nessus
- Nessus is a proprietary vulnerability scanner developed by Tenable Network Security. It is free of charge for personal use in a non-enterprise environment.
- NTM
- NTM allows you to automatically plot your network in minutes with network mapping software. Automatically discover and delineate your network topology and produce comprehensive, easy-to-view network diagrams. NTM supports multiple discovery methods including SNMP v1-v3, ICMP, WMI, CDP, VMware, Hyper-V, and more. Export network maps to Microsoft Office Visio, PDF, and PNG formats, and also schedule updated map exports to Orion® Network Atlas. Deliver robust reports on switch ports, VLANs, subnets, and inventory.
- Proxy Workbench
- Proxy Workbench is a proxy server unlike all others. It is unique because all of the data passing through it is displayed in real time, you can drill into particular TCP/IP connections, view their history, save the data to a file and view the socket connection diagram. The socket connection diagram is an animated graphical history of all of the events that took place on the socket connection.
- Proxy Switcher
- Anonymous Browsing using Proxy Switcher automatically switching among multiple available proxy servers.
- NetBIOS Enumerator
- NetBIOS stands for Network Basic Input Output System. It Allows computer communication over a LAN and allows them to share files and printers. NetBIOS names are used to identify network devices over TCP/IP (Windows).
- nbstat
- The Nbstat command is a great command to use when you need to display the NetBIOS over TCP/IP protocol statistics. The Nbstat command can also be used to display NetBIOS name tables for both local and remote computers. The Nbstat command can also be used to display the NetBIOS name cache, which will show you all of the NetBIOS names that have recently been associated with a specific IP address.
- net view
- Command line tool to identify shared resources on a network.
- Snmputil.exe
- You can use the Snmputil.exe support tool to verify that the SNMP service has been correctly configured to communicate with SNMP management stations.
- SNScan
- SNScan is a Windows based SNMP detection utility that can quickly and accurately identify SNMP enabled devices on a network. This utility can effectively indicate devices that are potentially vulnerable to SNMP related security threats.
- Network Browser
- With SolarWinds network monitoring software’s IP network browser you can regularly discover the SNMP enabled devices on your network.
- Metasploit
- The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its best-known sub-project is the open source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine.
- snmpwalk
- The snmpwalk command essentially performs a whole series of getnexts automatically for you, and stops when it returns results that are no longer inside the range of the OID that you originally specified.
- JXplorer
- JXplorer is a cross platform LDAP browser and editor. It is a standards compliant general purpose LDAP client that can be used to search, read and edit any standard LDAP directory, or any directory service with an LDAP or DSML interface. It is highly flexible and can be extended and customized in a number of ways.
- ntpdc
- ntpdc uses NTP mode 7 packets to communicate with the NTP server, and hence can be used to query any compatible server on the network which permits it. Note that since NTP is a UDP protocol this communication will be somewhat unreliable, especially over large distances in terms of network topology.
- smtp-user-enum
- smtp-user-enum is a tool for enumerating OS-level user accounts on Solaris via the SMTP service (sendmail). Enumeration is performed by inspecting the responses to VRFY, EXPN and RCPT TO commands.
- Skipfish
- Skipfish is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments.
- HTTPRecon
- HTTPRecon or HTTP Fingerprinting is a tool developed by computec.ch and modified by w3dt to help return highly accurate identification of given httpd implementations. This is very important within professional vulnerability analysis.
- ID Serve
- ID Serve freeware internet server identification utility.
- inSSIDer
- inSSIDer is a Wi-Fi network scanner application for Microsoft Windows and OS X.
- Netsparker
- Automatically find vulnerabilities in your websites & web applications, and eliminiate false positives with Netsparker’s dead-accurate web security scanner.
- wpscan
- WPScan is a black box WordPress vulnerability scanner.
3 - الوصول (Gaining Access )
- Cain and Abel
- Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Crypt analysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
- pwdump7
- pwdump is the name of various Windows programs that output the LM and NTLM password hashes of local user accounts from the Security Account Manager (SAM). In order to work, it must be run under an Administrator account, or be able to access an Administrator account on the computer where the hashes are to be dumped. Pwdump could be said to compromise security because it could allow a malicious administrator to access user’s passwords.
- fgdump
- Fgdump is basically a utility for dumping passwords on Windows NT/2000/XP/2003/Vista machines. It has all the functionality of pwdump in-built and can also do a number of other neat things also like grabbing cached credentials, executing a remote executable and dump the protected storage on a remote, (or local), host.
- rtgen
- This tool is used to generate the rainbow tables.
- Winrtgen
- Is a graphical Rainbow Tables Generator that supports LM, FastLM, NTLM, LMCHALL, HalfLMCHALL, NTLMCHALL, MSCACHE, MD2, MD4, MD5, SHA1, RIPEMD160, MySQL323, MySQLSHA1, CiscoPIX, ORACLE, SHA-2 (256), SHA-2 (384) and SHA-2 (512) hashes.
- rainbowcrack
- RainbowCrack is a computer program which generates rainbow tables to be used in password cracking. RainbowCrack differs from “conventional” brute force crackers in that it uses large pre-computed tables called rainbow tables to reduce the length of time needed to crack a password drastically.
- Ophcrack
- Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms.
- chntpw
- Chntpw (also known as Offline NT Password & Registry Editor) is a small Windows password removal utility that can run from a CD or USB drive.
- Yersinia
- Yersinia is a network tool designed to take advantage of some weakness in different network protocols. It pretends to be a solid framework for analyzing and testing the deployed networks and systems.
- Spytech SpyAgent
- SpyAgent is a computer spy software program that can monitor your computer in total stealth, recording everything from keystrokes and chats, to emails, website, and application usage.
- OpenPuff
- OpenPuff Steganography and Watermarking, sometimes abbreviated OpenPuff or Puff, is a freeware steganography tool for Microsoft Windows created by Cosimo Oliboni and still maintained as independent software.
- SNOW
- The program SNOW is used to conceal messages in ASCII text by appending white space to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected.
- setoolkit
- The Social-Engineer Toolkit (SET) was created and written by the founder of TrustedSec. It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering.
- dsniff
- dsniff is a collection of tools for network auditing and penetration testing. dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, e-mail, files, etc.). arpspoof, dnsspoof, and macof facilitate the interception of network traffic normally unavailable to an attacker (e.g, due to layer-2 switching). sshmitm and webmitm implement active monkey-in-the-middle attacks against redirected SSH and HTTPS sessions by exploiting weak bindings in ad-hoc PKI
- macof
- Floods the local network with random MAC addresses (causing some switches to fail open in repeating mode, facilitating sniffing).
- arpspoof
- In computer networking, ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker’s MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead. Use this tool to test ARP poisoning.
- Low Orbit Ion Cannon
- Low Orbit Ion Cannon (LOIC) is an open-source network stress testing and denial-of-service attack application, written in C#.
- THC Hydra
- When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more than 50 protocols, including telnet, ftp, http, https, smb, several databases, and much more.
- Brutus
- This Windows-only cracker bangs against network services of remote systems trying to guess passwords by using a dictionary and permutations thereof. It supports HTTP, POP3, FTP, SMB, TELNET, IMAP, NNTP, and more.
- Burp Suite
- Burp or Burp Suite is a graphical tool for testing Web application security.
- Havij
- Havij is an automated SQL Injection tool that helps penetration testers to find and exploit SQL Injection vulnerabilities on a web page.
- Aircrack-ng
- Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs.
- Cain and Abel
- Maintaining Access
- Covering Attacks
- Auditpol.exe
- Displays information about and performs functions to manipulate audit policies.
- clearlogs.exe
- Clear all Windows system logs.
- CCleaner
- CCleaner developed by Piriform, is a utility program used to clean potentially unwanted files (including temporary internet files, where malicious programs and code tend to reside) and invalid Windows Registry entries from a computer.
- MRU-Blaster
- MRU-Blaster is a program made to do one large task, detect and clean MRU (most recently used) lists on your computer.
- Auditpol.exe
- Miscellaneous
4 - الحفاظ على الوصول (Maintaining Access)
It reads and writes data across all network connections, using TCP or UDP protocol while encrypting the data that is transmitted.
It is a backdooring tool that injects backdoor's shellcode into an existing process.
It is a Netcat-clone, which offers strong encryption and runs on Unix like operating systems and on Microsoft Win32.
It is a network tool designed to relay TCP connection through DNS traffic.
It is used to tunnel network connections through a restrictive HTTP proxy.
It is an Intersect Post-exploitation framework.
It enables usages of PowerShell for offensive security and posts exploitation during Penetration Tests.
It extracts the password policy from a windows system.
It is a series of Microsoft Powershell scripts that can be used in post-exploitation scenarios during authorized penetration tests.
It is a NAT to NAT client-server communication.
It is an attack that enumerates user accounts through null sessions and SID to RID enum.
It is a secure backdoor for Linux and Windows systems.
It is a dynamic shellcode injection tool and dynamic PE infector used to inject shellcode into native Windows applications.
It is a Metasploit Payload Injection Tool for SanDisk Devices.
It is a collection of webshells for ASP, ASPX, CFM, JSP, Perl, and PHP servers.
It is a stealth web shell that stimulates telnet-like connections used for web application post exploitation.
It is a remote windows command executor.